Leave No Chance To Hackers. Step 2 of this network penetration testing checklist involves using this information to run tests on.

Firewall Penetration Testing Steps Methods And Tools That Work
Discovery After your organization has developed a strategy for the network pentest its time to initiate reconnaissance.

. You can use tools such as Metasploit Nessus and PowerShell for this. SSLTLS Scanner on HTTPS ports if needed. If you want to test your router in isolation and your router isnt built in to the modem then you can test it as follows.
Rarely are these part of a pentesting scope. No need to go insane for a home network IMO and wifey or hubby isnt going to be happy if her user account cant make changes on her laptop for example. Once you do this your Lovebox will turn off the newly created WiFi network and connect to.
Here are the basics for protecting your home Wi-Fi network. Or you can extend the Wired network by running cables into other rooms or using your power cables by installing home plug adapters. Create a strong Wi-Fi password and.
Make and storeusing either external media or a cloud-based serviceregular backup copies of all valuable information residing on your device. These are just a few examples of the things you can do when pentesting your own network. Ad Start Testing in 2 Minutes.
This step is very helpful in case your VM gets corrupt. Tips on how to secure your home network from hackers. Regularly back up your data.
Iklan Tengah Artikel 2. Keep reading for more information on each below. Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium.
CNAME Makes the domain. Penetration testing also known as pen testing is a simple term that means you are looking at your computer system to determine if it. Your company policy would also have to allow for this type of testing.
Below we have explained how to ensure it is turned on. Switch to the 5 GHz band. And on a home network they are pretty likely to accomplish that goal.
Iii Pick a payload. How To Scope A Network Penetration Test Pentester Tips Cobalt Overall if youre opening one port for the game server on your firewall then all the testing and vuln scanners will tell you nothing. If you try to perform pen test on the public IP then ASA being a security device will block the attacks.
Top 5 Tools Used in WIFI. Astra Security is one of the top penetration testing. Easy enough to follow at home but because its a home merging workstation users and workstation admins is an obvious convenience I would recommend to anyone.
Now click on Windows Security in the menu on the left. WiFi signals radiate in all directions. Live data can be read from Ethernet IEEE 80211 PPP HDLC ATM Bluetooth.
Ad Official CompTIA Site. If so this isnt necessarily a problem but it means that the previous test didnt test your router it tested the network connection to your router. If you place your router against an outside wall half of the signal goes out of your home.
Iklan Tengah Artikel 1. The next is Wireshark a network protocol and packet analyzer that is important when it comes to penetration test tools. Proactively Defend Against Ransomware Exploitation Social Engineering Attacks.
Dont forget to disable the port when youre done. Open Windows Command Prompt. Once you connect to this network using your phone or computer you navigate to the router-page at 19216841 and input your credentials to your actual WiFi network.
After collecting all the information you can about your target network its time to use this information for something dicey. Proper reporting of results. Exploitation of the Wireless Network.
TCP Scanner ports 1-65535 2. Post Comments Atom Iklan Atas Artikel. Next on the menu that opens on the right click on.
Most people have zero need for an XP VM in their home network since most people dont have industrial systems at home. Ensuring that your firewall is on and all the settings are properly configured will strengthen the network security of your network. However if you lack the knowledge or experience to do this yourself you can hire a professional penetration tester to do it for you.
Click on the Windows icon in the far left of your taskbar followed by Settings the cog symbol that appears just above it. 0 Response to how to pentest your home network Post a Comment. If you want to do a full but quick vulnerability scan try a scan template that runs multiple tools at the same time.
Targeted Correction Recommendation. However should you want to pentest these areas you would need to obtain explicit permission from the end user to inventory classify and perform a risk analysis on the networks supporting their home-based environment. Change the default name and password of your home network.
Ad Let Our Experts Conduct Internal External Pen Testing to Evaluate Your Vulnerabilities. When you first plug the device in and open the lid it creates a new WiFi network. This name is also known as the SSID Service Set Identifier and you can alter it by following these steps.
Scroll down and click Update Security to open the menu. Once you do this your Lovebox will turn off the newly created WiFi network and connect to your actual WiFi. Discovery After your organization has developed a strategy for the network pentest its time to initiate reconnaissance.
If your stuff is decently patched current software and you dont use defaultbullshit credentials youre pretty safe. Placing the router in the center of the house will both ensure better coverage inside the house and reduce the amount of the signal that makes it out of the house. Save 24 On CompTIA PenTest Certmaster Bundle.
Place your router in a central location. The easiest thing you can do to secure your home internet connection is to change the default name. Based on the results start the Network Vulnerability Scan with OpenVAS and check for open ports.
I Pick which exploit to use. Penetration testing or pen testing is used to ensure that your enterprise is protected against cyberattacks and with a little work its possible to take care of the basics yourself.
Building A Test Lab For Pentesting Guide White Oak Security

How To Set Up A Pentesting Lab Rapid7 Blog
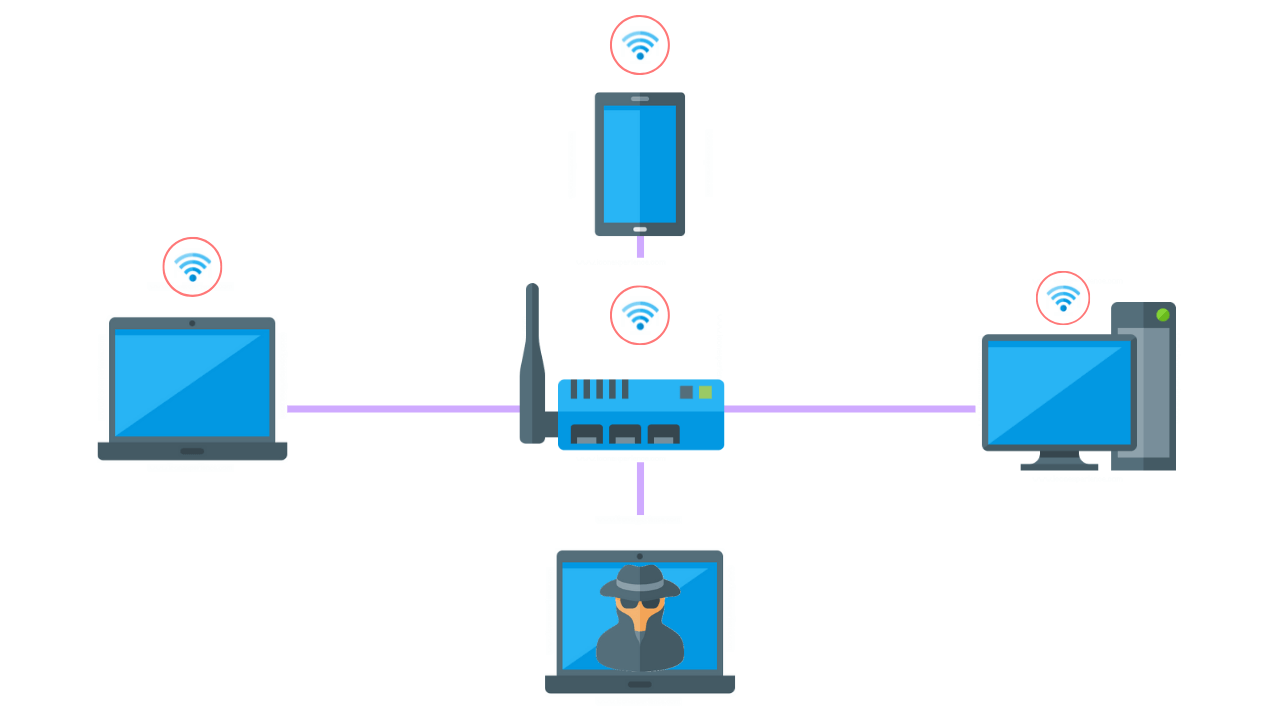
How To Perform A Successful Wifi Penetration Test
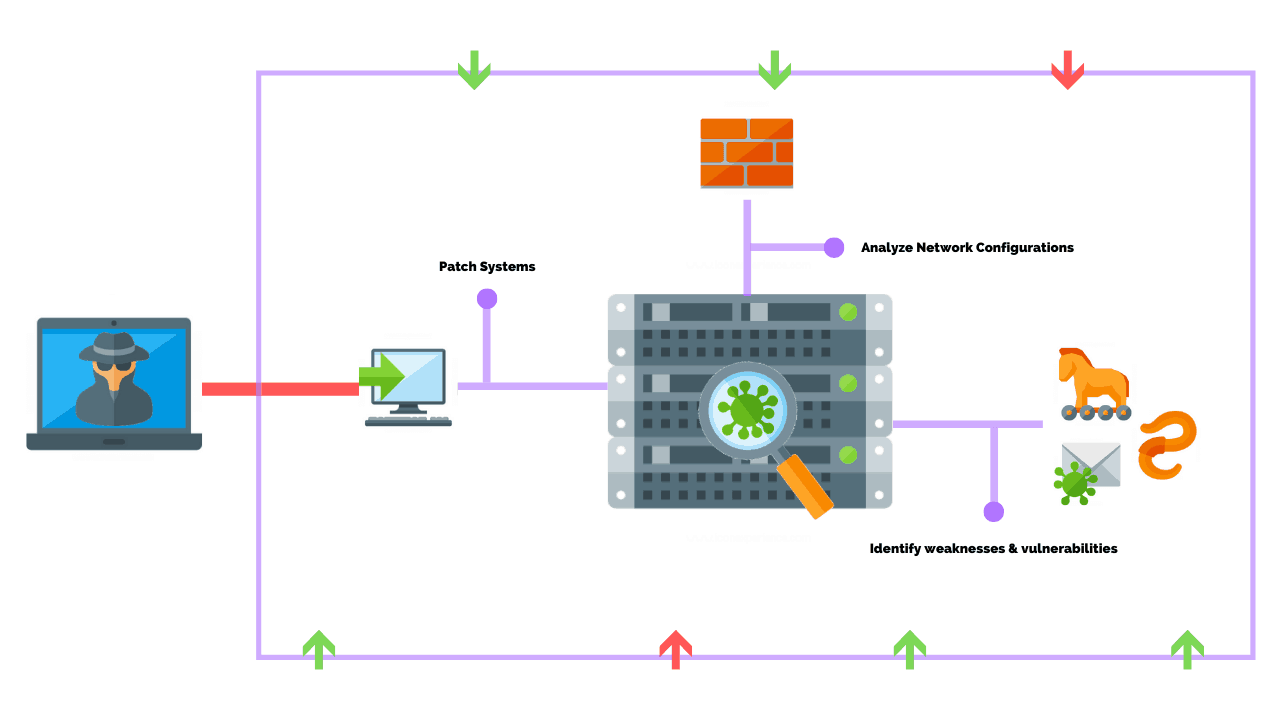
How To Perform A Successful Network Penetration Test Purplesec

Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium
Home Network Design Part 1 Black Hills Information Security
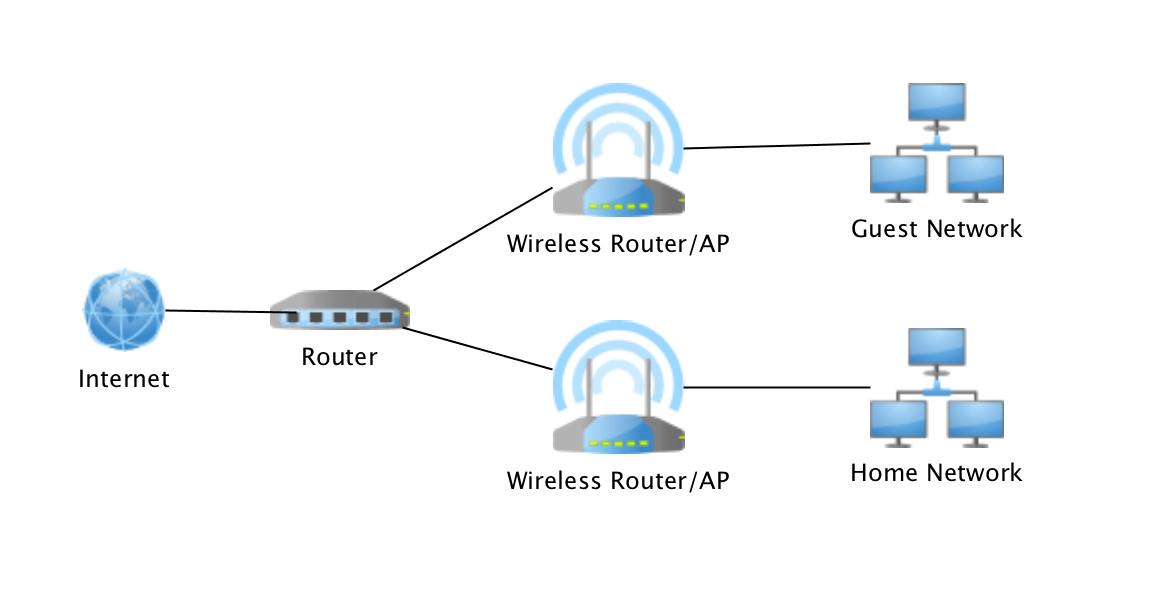
Home Network Design Part 1 Black Hills Information Security

Ultimate Guide On How To Perform A Successful Network Penetration Test
0 comments
Post a Comment